Behavioral biometrics is an evolving technology that authenticates users based on patterns in their behavior. It identifies specific regularities in the ways that people type and move, rather than identifying parts of their bodies (fingerprints, facial recognition, palm vein), things that they have (time and attendance cards), or things that they know (passwords).
Instead of conventional authentication methods, which only authenticate when access is initiated, behavioral biometrics technologies continuously verify and evaluate the user's ongoing interaction with their mobile device or computer in real time.
Types of Behavioral Biometrics
Although the field of behavioral biometrics continues to develop, two basic types of behavioral biometric data can already be identified: kinesthetic (body movements) and device-based gestures.
Body Movements
- Status: The individual properties of an individual’s body position and weight division while standing or while seated.
- Gait: An individual’s unique walking style, including characteristic movements made while in motion: stride length, upper body posture, and speed of travel relative to these.
- Handling: The way a person holds or manages a mobile device is a different unique factor of behavioral biometric data.
Device-Based Gestures
- Keystroke Dynamics: Typing models that vary uniquely from user to user. These involve a mixture of keystrokes speed, keystroke duration, variations in these for particular key sequences, and characteristic patterns that happen when typing general groups of keystrokes such as words or control sequences.
- Touchscreen Swipes / Mobile Interactions: The unique ways in which users swipe, tap, pinch-zoom, type, or implement pressure on the touchscreens of mobile devices like tablets and phones.
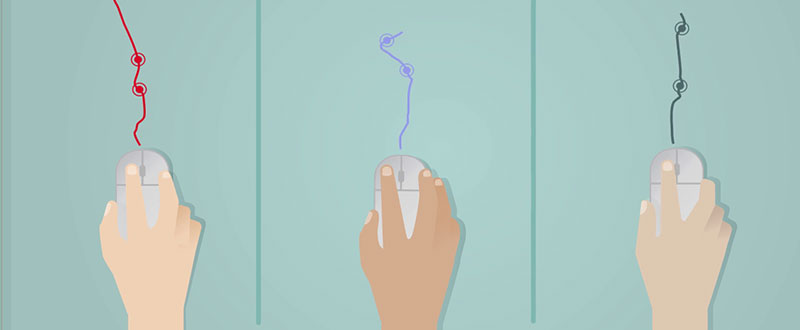
- Cursor Movement: Unique models in mouse or trackpad cursor movement including paths, tracking speed, direction changes, clicks, and the connections between these.


Behavioral vs. Physiological
Physiological Biometrics
Physiological biometrics depends on the structures of the body for identification—for example, on fingerprints, on facial dimensions, or on the parts of the eye. Although these structures make each individual body unique, they are static, which leaves them more vulnerable to being scanned or photographed, then reconstructed for malicious use.
Behavioral Biometrics
Behavioral biometrics identifies patterns in the ways that particular bodies perform particular tasks—patterns in walking, speaking, typing, or even touchscreen and mouse behavior. These patterns are prohibitively difficult to capture and replicate, and they evolve over time.
Here’s how the Royal Bank of Scotland uses behavioral biometrics: As soon as users log in, a software starts recording 2,000-plus movements on the keyboard, mobile app, and website. On a smartphone, the software will measure the angle at which a user holds the device, what fingers are used to swipe, tap, and how hard or light the user applies pressure. On a computer, the software collects data on the beat of the keystrokes and how they use the mouse. The data collection is invisible to those being watched. Using sensors in your phone or code on websites, companies can gain thousands of data points, known as “behavioral biometrics,” to help determine whether a digital user is the person she claims to be.

Use Cases of Behavioral Biometrics
Stolen Credentials
No matter what countermeasures are in the site, login credentials are rhythmically stolen or endangered. They endanger systems, data, and whole infrastructures. Behavioral biometrics can be used to ensure that the person trying to use a system has been legally granted access to it.
Password/Account Sharing
The informal sharing of named accounts is a common security risk. Best-in-class behavioral biometrics technologies can differentiate between intended users and everyone else—even as login credentials are being entered—and block authentication accordingly.
User Substitution
Ad-hoc substitution of one user for another, without prior knowledge or consent, is both common and risky, particularly in outsourced environments. Behavioral biometrics algorithms can ensure that the person actually using a system is the person presumed to be using it.
Phishing Attacks
Though behavioral biometrics can’t stop a user from clicking on malicious links or supplying sensitive data to malicious actors, it can rapidly detect intruders that use phishing data to access and act on a secured system.
User Carelessness
Even the most conscientious users may inadvertently leave workstations unattended or unlocked before stepping away. Behavioral biometrics can identify the arrival of a new, unauthorized user rapidly—even at an unlocked workstation—and take appropriate measures.
License Mismanagement
The illicit sharing of per-seat licenses is both common and a liability risk for many large organizations. Behavioral biometrics can ensure that licensing practices are sound and only named users make use of licensed products and services.
Identity Fraud
Financial services organizations, health care organizations, or others that provide services to end-users can rapidly profile each user's behavior and stop malicious attempts to access data or services with stolen user credentials.
Related Articles: