Biometric is the measurement and mathematical analysis of people's unique physical and behavioral characteristics. The technology is mainly used for identification and access control, or for identifying individuals who are under surveillance. The basic premise of biometric authentication is that every person can be accurately determined by their intrinsic physical or behavioral traits. The term biometrics is derived from the Greek words bio, meaning life and metric meaning to measure.
History of biometric technology
In the second century B.C., the Chinese emperor Ts'In was already authenticating specific seals with a fingerprint. In the U.K., the Metropolitan Police started the use of biometrics for identification in 1901. In the U.S., it was initiated by the New York police in 1902 and by the FBI in 1924. The French police started to initiate the same process in late 1902.
How biometrics work
Authentication by biometric verification is becoming more common in corporate and public security systems, consumer electronics. In addition to security, the driving force behind biometric verification has been ease, as there are no passwords to remember or security tokens to carry. Some biometric methods, such as measuring a person's gait, can operate with no direct contact with the person being authenticated.
Components of biometric devices
- A reader or scanning device to record the biometric factor being authenticated.
- Software to convert the scanned biometric data into a standardized digital format and to compare match points of the detected data with stored data.
- A database to securely store biometric data for comparison.
Types of biometric
The two main types of biometric identifiers depend on physiological symptoms and behavioral characteristics.
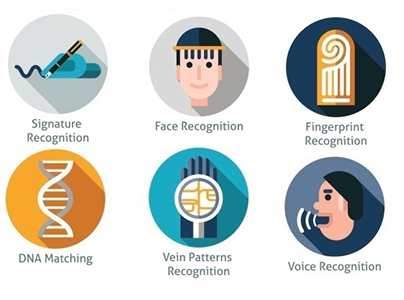
- Physiological identifiers relate to the creation of the user being authenticated and include: facial recognition, fingerprints, finger geometry (the size and position of fingers), Iris recognition, vein recognition, voice recognition, DNA matching.
- Behavioral biometric include the unique ways in which individuals act, including recognition of typing patterns, walking gait, and other gestures.
Advantages of biometrics:
- Hard to fake or steal, unlike passwords.
- Ease of use and convenience.
- Are non-transferable.
- Templates take up less storage.
Disadvantages of biometrics:
- It is costly to get a biometric system up and running.
- Databases holding biometric data can still be hacked.
- Errors such as false rejects and false accepts can still happen.
- If a user gets injured, then a biometric authentication system may not work (for example, the user burns their hand, then a fingerprint scanner may not be able to identify them).
Security and privacy issues of biometrics
Biometric identifiers depend on the uniqueness of the factor being considered. For example, fingerprints are generally considered to be highly unique to each person. Fingerprint recognition, primarily as implemented in Apple's Touch ID for previous iPhones, is the first widely used mass-market application of a biometric authentication factor. The security of the biometric factor can also be necessary for the acceptance of the element. Fingerprints do not change over a lifetime, while facial appearance can change drastically with age, illness, or other factors.
Use cases of biometrics
Historically, applications using biometrics have been predominantly initiated by authorities for military access control, criminal or civil identification under a tightly regulated legal and technical framework. Most importantly, awareness and acceptance have been boosted in the past seven years, as millions of smartphone users are unlocking their phones with a fingerprint or a face.
- Law enforcement: In systems for criminal I.D.s such as fingerprint or palm print authentication systems.
- Border control: In systems for electronic passports which stores fingerprint data, or in facial recognition systems.
- Healthcare: In health insurance programs which may use fingerprints for identification.
- Biometric access control systems: Biometric access control systems help to prevent unauthorized individuals from accessing facilities (physical access control) or computer systems and networks (logical access control) based on biometric authentication. Unlike codes, passwords, or access cards that rely on data that can be forgotten or lost, biometric authentication is based on who people are (and not what they have).
- In the mobile world, smartphones (a form of I.T. system) now usually include fingerprint and facial recognition features. The iPhone 5 was first to introduce fingerprint recognition in 2013 (with TOUCH ID), and facial recognition became trendy with the iPhone X introduced in November 2017 (with FACE ID). Today many Android phones have this feature (combined with iris scanning) too.